Phishing simulation examples
We have a wide range of templates for both email and landing pages within the RapidPhish. Here are some examples:
Unusual Account Activity
Unusual activity detected on your Bank of America account, click to login and Secure Your Account
Preview email template
Preview landing page

Microsoft 365 quarantined emails
The recipient is notified that an email has been quarantined in their mailbox, they can choose to accept or block the sender.
Preview email template
Preview landing page
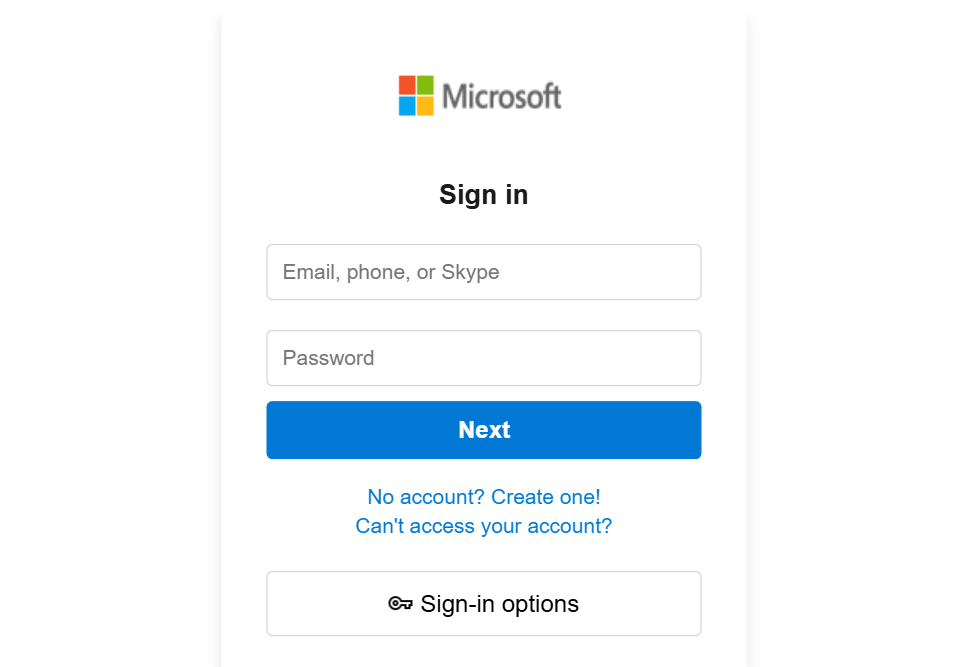
Slack Reset your Workspace Password
Email from Slack advising that the user had requested a password reset.
Preview email template
Preview landing page

Bonus Points Update
The email content informs the recipient that they have received 10,000 free Hilton Honors bonus points.
Preview email template
Preview landing page

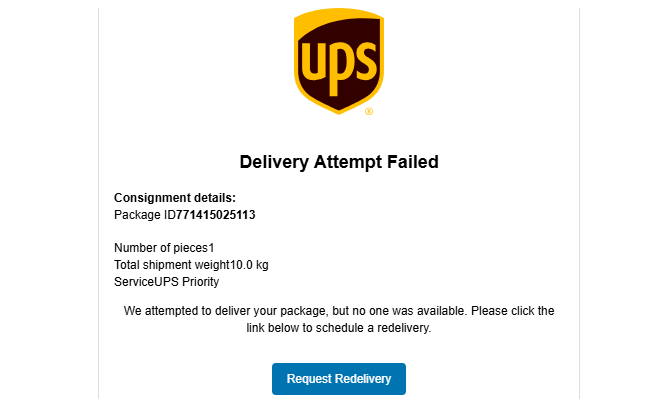
Failed Delivery Attempt
Email advising of a failed UPS delivery attempt, asking the recipient click to request a redelivery slot.
Preview email template
Preview landing page
Frequently asked questions:
-
What is a phishing simulation?
Phishing simulation is a cybersecurity training technique where organizations send mock phishing emails to employees to test and improve their ability to identify and respond to phishing attacks. These emails mimic real-world threats, such as fake login prompts or urgent requests, encouraging users to engage.
-
Why is phishing simulation important to my organisation?
Simulations help organizations identify vulnerabilities, raise awareness, and reduce the risk of real attacks by fostering a security-conscious culture. Regular simulations reinforce vigilance and strengthen overall cybersecurity defenses.
-
Can I design my own email and landing page?
Yes if you would like to create a bespoke theme for your campaign you can use the builder to design your own email template and landing pages.
-
Can I export the results?
Of course, you have the ability to export a pdf report with all simulation configuration and user engagement metrics.
-
How are passwords captured?
A user is considered compromised if they enter an email address/password and click the Submit or Login button a landing page.
The RapidPhish portal then marks this user as compromised and stores a masked version of the user password within the campaign results. -
What scheduling options are there for a campaign?
Campaigns can be scheduled to suit your preferred date and time of delivery.
-
How do I add recipients?
Within the RapidPhish portal you are required to generate at least one recipient group. Within this recipient group you are then able to add your users, these can be added via a csv upload (a template is available) or via manual user upload where a first name, last name and email address is entered for each user.
This recipient group can then be selected when building a campaign, all email addresses within the recipient group will then receive the campaign email.
